In recent times, a surge in scams has impacted numerous Australians as their online accounts have fallen prey to hacking, resulting in fraudulent transactions conducted without their knowledge. This prevalent cyber attack, known as “credential stuffing,” has long been a favored tactic among hackers. Here’s a concise guide to understanding this practice, recognizing potential compromises, and implementing protective measures for your online security.

Read more here: What is credential stuffing? How does it work? How can I protect myself from being scammed through my online accounts?
What is Credential Stuffing?
The Australian Cyber Security Centre defines credential stuffing as a cyber attack in which cybercriminals leverage previously stolen passwords from one website to gain access to multiple accounts. Essentially, hackers exploit the common practice of individuals using the same email and password combinations across various online platforms.
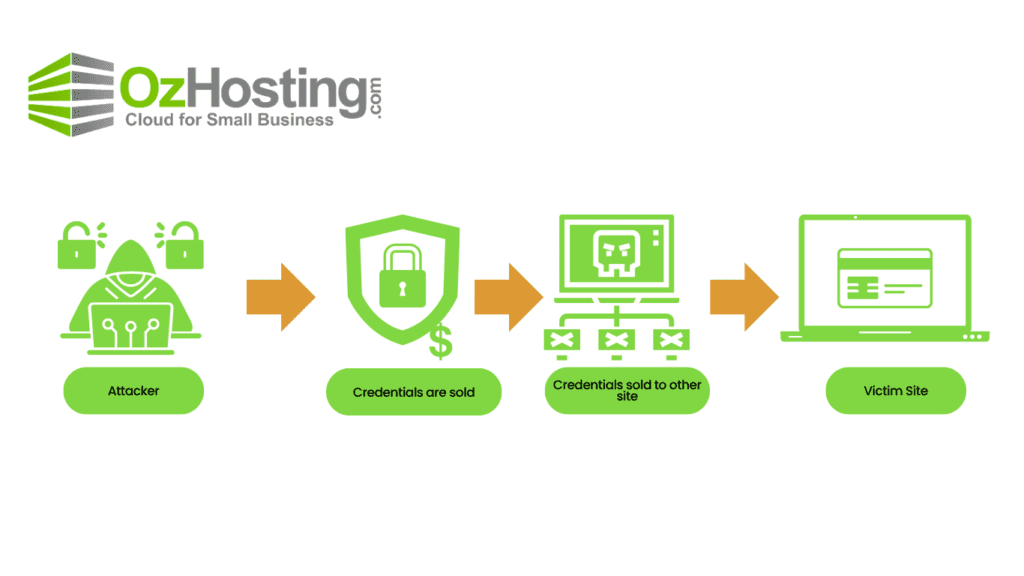
How does a Credential Stuffing Attack Work?
Hackers initiate credential stuffing attacks by purchasing login credentials on the dark web and utilizing automated tools, known as bots, to test millions of username and password combinations on different websites. This ‘brute force’ approach allows hackers to identify matches swiftly, exploiting the tendency of users to reuse passwords.
How Will I Know if I’ve Been Affected?
Detecting a credential stuffing attack can be challenging, as victims often remain unaware of compromised login details. Suspicious transactions or unusual patterns may trigger investigations by a business’s cybersecurity team. Some individuals may receive order confirmation emails for unauthorized purchases or face difficulties logging in without receiving password reset emails.
Protecting Yourself: What Can You Do?
To safeguard against credential stuffing, cybersecurity experts recommend adopting unique, strong passwords for each online account. Choosing passwords with a mix of upper and lower-case letters, numbers, and symbols enhances security. Regularly monitoring accounts for suspicious activity and utilizing services like “Have I Been Pwned” can provide early warnings of potential breaches.
Here’s a comprehensive guide, including the integration of Rushfiles, to fortify your digital security:
- Instant Collaboration:
- Boosting Team Efficiency: RushFiles facilitates instant collaboration within your business ecosystem. Team members can seamlessly share, access, and collaborate on files in real-time, fostering a more efficient and dynamic workflow.
- Enhanced Productivity: By eliminating the delays associated with traditional file-sharing methods, RushFiles empowers your team to work cohesively on projects, leading to increased productivity and faster project completion.
- Strong Security Measures:
- Data Protection at its Core: RushFiles prioritizes the security of your business data. Advanced encryption protocols ensure that sensitive information remains confidential and protected from unauthorized access.
- Secure File Sharing: With secure file-sharing features, RushFiles ensures that your business-critical data is shared only with authorized individuals, mitigating the risk of data breaches and maintaining the integrity of your confidential information.
- Compliance Assurance: Meeting regulatory requirements is paramount. RushFiles provides a secure environment that aligns with data protection regulations, offering peace of mind and compliance assurance for your business.
Read more: Accelerate Your Business: The Top-Tier Benefits of RushFiles – OzHosting Solutions
Cybersecurity professionals also suggest using a separate credit card for online transactions with a low limit and avoiding saving payment details on accounts. While inconvenient, these practices significantly enhance security and minimize the risk of unauthorized purchases.
Can Banks or the Government Help?
Banks play a crucial role in identifying and halting suspicious transactions, leveraging AI systems to protect customers. Some banks offer dynamic CVC codes to prevent online fraud. The government is also working on privacy reforms to enhance data protection, emphasizing the need for businesses to be accountable for securing user information.
Conclusion: Empowering Your Defense Against Cyber Threats with RushFiles Solutions
In the ongoing battle against cyber threats like credential stuffing, proactivity is the key to safeguarding your digital realm. By adopting stringent measures such as crafting unique passwords, implementing multi-factor authentication, and maintaining vigilant account monitoring, you fortify your defense against potential security breaches.
However, in this ever-evolving landscape, where cyber threats continually advance, a comprehensive solution is paramount. This is where RushFiles emerges as a transformative force, offering cutting-edge solutions to bolster your cybersecurity posture.
Experience the RushFiles Advantage – Start Your 30-Day Free Trial
In embracing RushFiles, you not only fortify your defense against cyber threats but also embark on a journey of seamless collaboration and robust security. Elevate your business operations by experiencing the transformative power of RushFiles.
Start your 30-day free trial today and stay ahead in the realm of cybersecurity. Stay informed, stay secure with RushFiles.
Get in touch with our team to discuss your options – [email protected]


